When an organization uses passwordless authentication, they need to figure out how to onboard users. In other words, you need to solve the chicken/egg problem. If a user has not registered any passwordless authentication method, how can they authenticate to register a passwordless authentication method?
Temporary Access Pass (TAP) solves this problem.

What is Temporary Access Pass
Temporary Access Pass is a generated passcode that a user can use to sign in. This generated passcode has a configurable length and validity period. It is also possible to force a one-time use.
Importantly, however, once a valid Temporary Access Pass is generated on a user account, this Temporary Access Pass replaces the password and any multi-factor authentication requirement. Thus, the Temporary Access Pass is the solution to the above chicken/egg problem 🙂
How to enable the use of Temporary Access Pass
Before you can start using Temporary Access Pass, you need to enable this authentication method in Microsoft Entra ID.
Go to Microsoft Entra admin center and under Protection, go to Authentication methods – Policies. Click on Temporary Access Pass from the list of authentication methods.
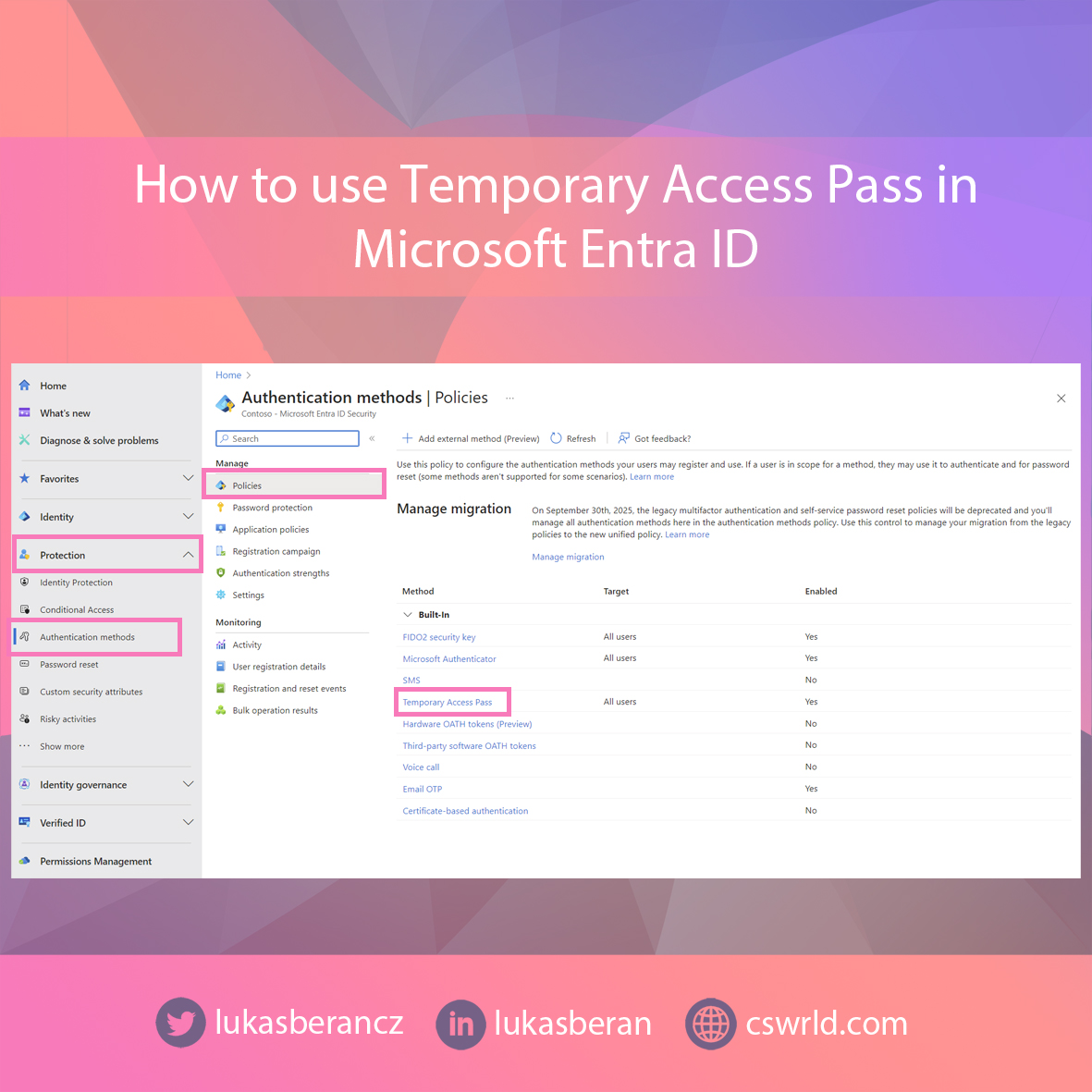
Switch to the Configure tab and set the Temporary Access Pass to work as expected. You can leave the validity at the default, but I recommend thinking about the length of the generated passcode and whether or not to force a one-time use. Enforcing a one-time use is generally more secure, but on the other hand, there may be situations where a Temporary Access Pass needs to be reused.

Once you have configured Temporary Access Pass, you can go back to the Enable and Target tab and enable the use of Temporary Access Pass.
Here’s something to think about though. Whether it’s appropriate or desirable to enable Temporary Access Pass for all users. For security reasons, I would not enable it for all users, as such a policy then targets administrators as well, but rather I would recommend enabling the use of Temporary Access Pass only for a group of regular users.
Do not enable Temporary Access Pass for all users.

Enable Temporary Access Pass in Authentication strengths
Once you have Temporary Access Pass enabled, you still need to enable this authentication method for use within Authentication Strengths.
If you are using the built-in Multifactor authentication authentication strength, then there is no need to do anything further as this group of authentication methods already includes Temporary Access Pass. However, if you are using a custom Authentication Strength, you may need to add the Temporary Access Pass authentication method there.
Under Authentication methods, switch to Authentication strengths and select the Authentication strength you want to modify.

Open your own Authentication strength for editing and verify that Temporary Access Pass is enabled. Note that there is a separate menu for One-time use and Multi-use, so select what you want to enable.

It is up to you to consider whether you want to enable Temporary Access Pass for all sign in scenarios or just selected ones. In general, the Temporary Access Pass should only be used to set up or change authentication methods (including Windows Hello for Business enrollment) and should not be used for regular logins. Therefore, it is advisable to make an extra Conditional Access Policy + extra Authentication strength only for the selected scenarios and not allow the use of Temporary Access Pass in general for any login.
How to use Temporary Access Pass
You are now ready to start using Temporary Access Passes.
When you want to generate a Temporary Access Pass on an account, open the account details in Microsoft Entra ID and go to Authentication methods. In the top menu, click Add authentication method.

From the menu of authentication methods to add, select Temporary Access Pass. You can then choose whether the newly generated Temporary Access Pass will be one-time use or multi-use, and its validity period and start of validity, according to the set policy. Setting the start of validity is useful, for example, if you have new employees who start the next day, but you want to prepare the Temporary Access Pass a day earlier and set the start of validity for the next day, for example, from 7:00 am.


The newly generated Temporary Access Pass will appear as a new authentication method for that user. In the menu under the three dots on the right, you can view the details of the generated Temporary Access Pass or delete the passcode to invalidate it.

From the moment the Temporary Access Pass is valid, the Temporary Access Pass box will automatically replace the password box after the user enters the username on the login screen. Not only in web browser, but also in the Microsoft Authenticator application or during the enrollment of a new computer.


You can find a detailed video showing all the settings with spoken commentary describing each configuration option in detail on my Patreon. By subscribing you also support my work. Thank you!




